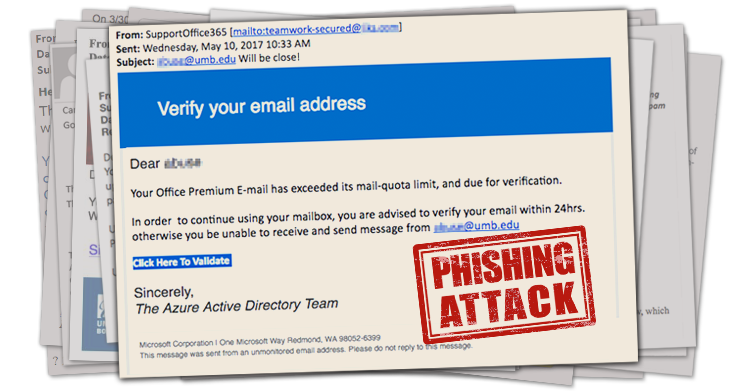
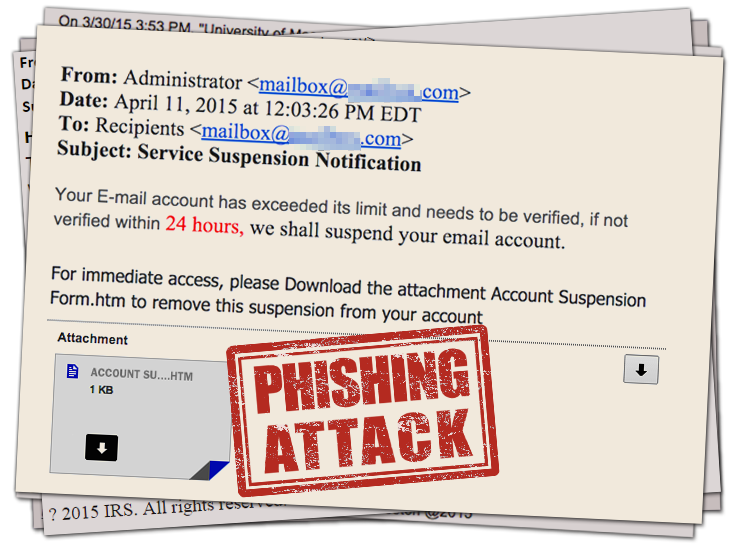
While most phishing attacks are laughably obvious, you can’t count on the ineptitude of scammers. Today’s example was submitted by Wendy L., who was able to see through this very realistic forgery, and inform IT Staff about this scam. Check it out below:
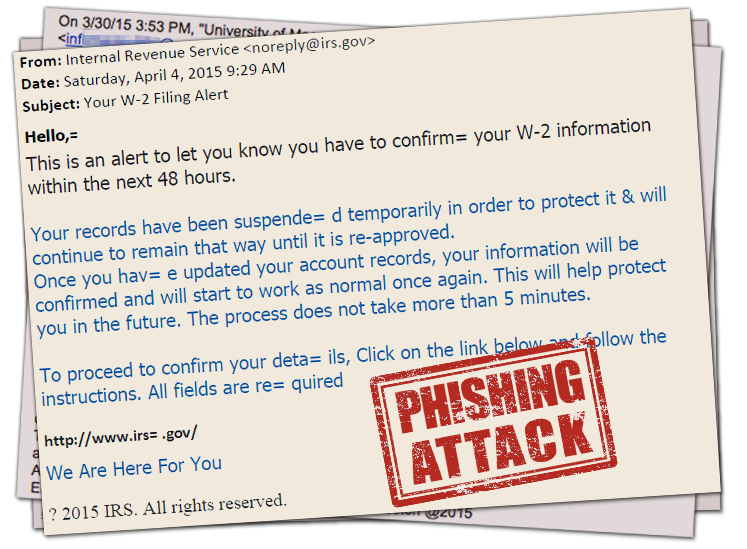
The first thing that makes this a more sophisticated attack than the norm is the “From” address. While this can often be a clear way to identify a scam, in this case the scammer was able to spoof a legitimate email address. Read more about Email Spoofing from Lifehacker.com. The From address is easily faked if you know how, so looking at that address is not a reliable way to sniff out a fake.
Another part of the attack is the link at the bottom of the email. Again, it looks legitimate — irs.gov is the real website for the IRS — however, the visible text is also easy to customize, while the URL it sends you to can be different. For example, click the following link to go to the UMB website: http://umb.edu/. See how the visible text said umb.edu, but when you click, it goes somewhere else entirely! To learn more about URL Spoofing, and how to protect yourself, visit the article, How to protect yourself from spoofing… Did I fool you again? The real link is http://www.chiaramailcorp.com/dont-spoofed/. Copying and pasting the URL into a new browser window is another way to avoid URL spoofing.
So with sophisticated scammers out there, how can you stay safe? Just keep your wits about you. Keep reading this blog and you’ll develop a healthy paranoia about scam emails. Never give out your personal info just because someone asks, and don’t trust phone numbers and URLs in an email.
And remember…
Don’t take the bait! IT will NEVER ask you for your password. Phishing emails attempt to deceive you into giving up your private information by leading you to fraudulent websites. Learn more at:
http://www.umb.edu/it/getting_services/security/phishing/